In my previous post I wrote about
Migrating Azure Durable Function App to Use Durable Task Scheduler: Running
Locally. And in this post, let's see how to run an Azure Durable Function App
with DTS in Azure.
As of today DTS supports function apps that uses App Service Plan or Functions Premium plan. And also it's not supported
in all the regions. You can run the following command to check the supported
regions.
az provider show `
--namespace Microsoft.DurableTask `
--query "resourceTypes[?resourceType=='schedulers'].locations | [0]" `
--out table

|
|
DTS: Supported Regions
|
So I have an Azure Durable Function App, the same application which is
mentioned in the
above post (except the changes done to use DTS). It uses an
App Service Plan and is on
East US 2. So we are all good to
start migrating the Azure Durable Function App to use DTS.
Assuming you have az cli installed and logged in, let's add durabletask extension.
az extension add --name durabletask
# If you have it installed already, upgrade it to the latest version
# az extension add --upgrade --name durabletask
Now, let's create the scheduler,
az durabletask scheduler create `
--name "<SCHEDULER_NAME>" `
--resource-group "<RESOURCE_GROUP_NAME>" `
--location "<REGION>" `
--ip-allowlist "[0.0.0.0/0]" `
--sku-name "dedicated" `
--sku-capacity "1"
This is going to take some time to complete.
 |
| az durabletask scheduler create |
Make note of the endpoint. Now let's create a taskhub:
az durabletask taskhub create `
--name "default" `
--resource-group "<REESOURCE_GROUP_NAME>" `
--scheduler-name "<SCHEDULER_NAME>"

|
|
az durabletask taskhub create
|
You can also do this in Azure Portal by searching for Durable Task Scheduler and create.

|
|
Durable Task Scheduler
|
 |
| Durable Task Scheduler |
Now the Scheduler and the TaskHub is created, next we need to grant our
function app access to this Scheduler and/or TaskHub. DTS only supports
either user-assigned or system-assigned managed identity
authentication.
So let's do the following.
-
Create an user-assigned managed identity.
-
Assign a role to managed identity. It can be one of the
following:
-
Durable Task Data Contributor: Role for all data access
operations. This role is a superset of all other roles.
-
Durable Task Worker: Role used by worker applications to interact
with the durable task scheduler. Assign this role if your app is used
only for processing orchestrations, activities, and entities.
-
Durable Task Data Reader: Role to read all durable task scheduler
data. Assign this role if you only need a list of orchestrations and
entities payloads.
-
Assign the identity to the function app.
# 1. Create an user-assigned managed identity
az identity create `
--resource-group "<RESOURCE_GROUP_NAME>" `
--name "mi-func-dts"
## get the identity id
$managedIdentityClientId = az identity show `
--resource-group "<RESOURCE_GROUP_NAME>" `
--name "mi-func-dts" `
--query clientId `
--output tsv
# 2. Assign a role to managed identity
## Scope can be either to the entire scheduler or to the specific task hub
### scheduler
#scope = "/subscriptions/<SUBSCRIPTION_ID>/resourceGroups/<RESOURCE_GROUP_NAME>/providers/Microsoft.DurableTask/schedulers/<SCHEDULER_NAME>"
### task hub
$scope = "/subscriptions/<SUBSCRIPTION_ID>/resourceGroups/<RESOURCE_GROUP_NAME>/providers/Microsoft.DurableTask/schedulers/<SCHEDULER_NAME>/taskHubs/<TASKHUB_NAME>"
az role assignment create `
--assignee "$managedIdentityClientId" `
--role "Durable Task Data Contributor" `
--scope "$scope"
# 3. Assign the identity to the function app
$managedIdentityResourceId = az resource show `
--resource-group "<RESOURCE_GROUP_NAME>" `
--name "mi-func-dts" `
--resource-type Microsoft.ManagedIdentity/userAssignedIdentities `
--query id `
--output tsv
az functionapp identity assign `
--resource-group "<RESOURCE_GROUP_NAME" `
--name "<FUNCTION_APP_NAME>"
--identities "$managedIdentityResourceId"
Now we are almost done.
{
"name": "DTS_CONNECTION_STRING",
"value": "Endpoint=<SCHEDULER_ENDPOINT>;Authentication=ManagedIdentity;ClientID=<MANAGED_IDENTITY_CLIENTID>",
"slotSetting": false
},
{
"name": "TASKHUB_NAME",
"value": "default",
"slotSetting": false
}
Now let's hit the endpoint and make sure it's working.
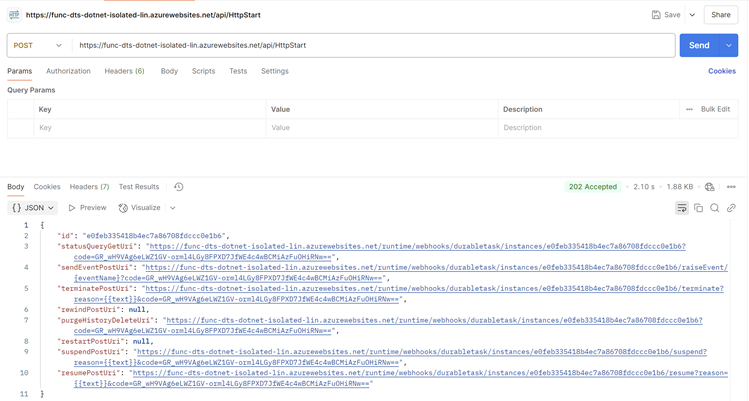
|
|
Test the function app
|
Wonderful.
Now we want to look at the DTS Dashboard. For that, let's grant our Azure
account access to DTS.
# Get the current user id
$assignee = az ad signed-in-user show `
--query id `
--output tsv
# Set the scope (can be either scheduler or task hub level), I am giving the user scheduler level
$scope = "/subscriptions/<SUBSCRIPTION_ID>/resourceGroups/<RESOURCE_GROUP_NAME>/providers/Microsoft.DurableTask/schedulers/<SCHEDULER_NAME>"
# Assign the role to the user
az role assignment create `
--assignee "$assignee" `
--role "Durable Task Data Contributor" `
--scope "$scope"
And there it is.

|
| DTS Dashboard |

|
|
DTS Dashboard: Orchestration Detail
|
Happy Coding.
Regards,
Jaliya











